This is a guide to CD and CI.
Introduction
1 | 1. ArgoCD <--- ok |
K3s
A lightweight kubernetes, like minikube.
Install
1 | #https://docs.k3s.io/quick-start |
Uninstall
1 | #Master |
Demo
1 | # Create a test Namespace, if not exist |
Kustomize
Declarative Management of Kubernetes Objects Using Kustomize | Kubernetes
1 | Kustomize/ |
base/kustomization.yaml
1 | commonLabels: |
base/deployment.yaml
1 | apiVersion: apps/v1 |
base/service.yaml
1 | apiVersion: v1 |
Dev environment:
overlays/dev/kustomization.yaml
1 | namePrefix: dev- |
overlays/dev/deployment.yaml
1 | apiVersion: apps/v1 |
overlays/dev/password.txt
1 | this is dummy secret but now I am changing it |
overlays/dev/service.yaml
1 | apiVersion: v1 |
Prod environment:
overlays/prod/kustomization.yaml
1 | namePrefix: prd- |
overlays/prod/deployment.yaml
1 | apiVersion: apps/v1 |
overlays/prod/password.txt
1 | this is dummy secret |
overlays/prod/service.yaml
1 | apiVersion: v1 |
Create
1 | cd overlays/dev |
Argocd
Getting Started - Argo CD - Declarative GitOps CD for Kubernetes (argo-cd.readthedocs.io)
Install
1 | #argocd with kubernetes 1.18 |
Enable external web ui
1 | #Change port to 8443 and 8080 |
The URL is: https://192.168.64.6:8443/, login name is admin. Getting password from:
1 | kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d; echo |
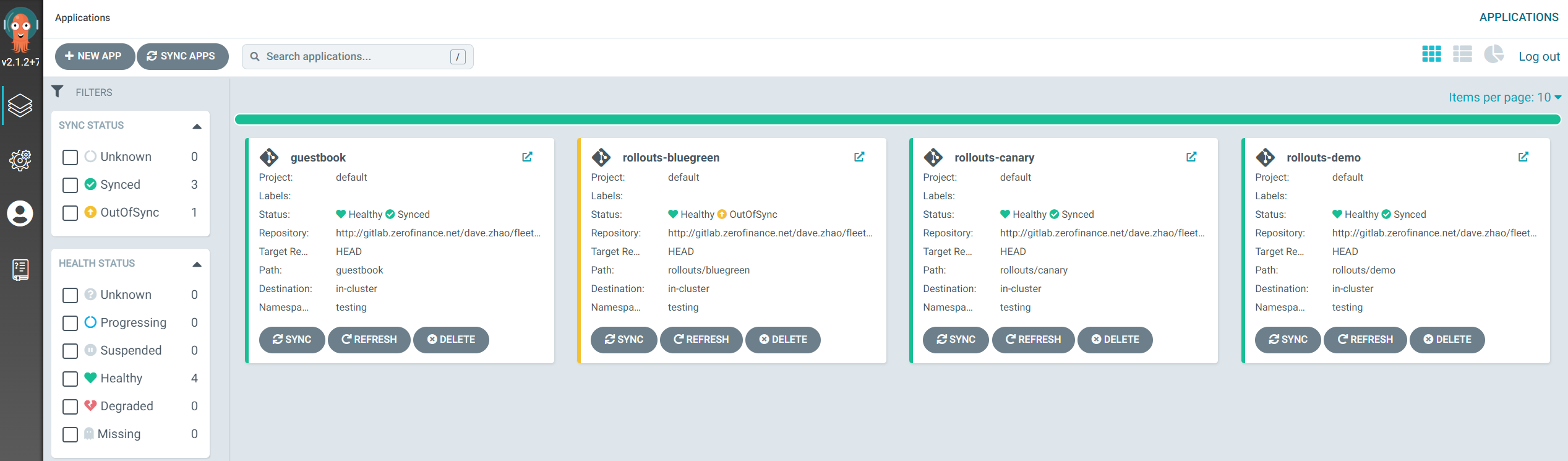
Demo
Demo1
1 | fleet/ |
application.yaml
1 | # application.yaml |
dev/deployment.yaml
1 | # deployment.yaml |
dev/service.yaml
1 | # service.yaml |
Create Apps Via Command
1 | kubectl apply -f application.yaml |
Creating Apps Via UI
Open a browser to the Argo CD external UI, and login by visiting the IP/hostname in a browser and use the credentials set in step 4.
After logging in, click the + New App button:
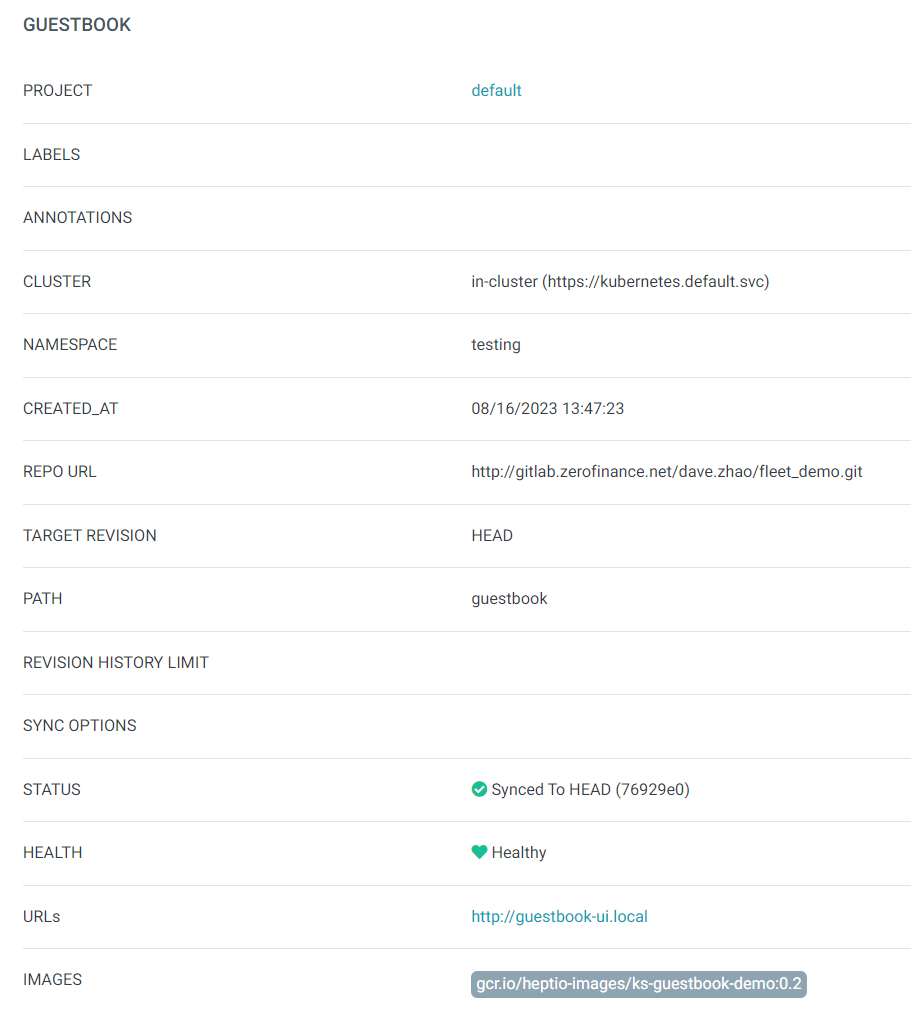
Notice: If you create apps via UI, you don’t need application.yaml located in root folder.
More usage please visit: Getting Started - Argo CD - Declarative GitOps CD for Kubernetes (argo-cd.readthedocs.io)
Demo2
guestbook-ui-deployment.yaml
1 | apiVersion: apps/v1 |
guestbook-ui-svc.yaml
1 | guestbook/ |
guestbook-ui-deployment.yaml
1 | apiVersion: apps/v1 |
guestbook-ui-svc.yaml
1 | apiVersion: v1 |
argo-rollouts
Install
1 | kubectl create namespace argo-rollouts |
Demo
1 | #demo |
Dashboard
1 | #dashboard |
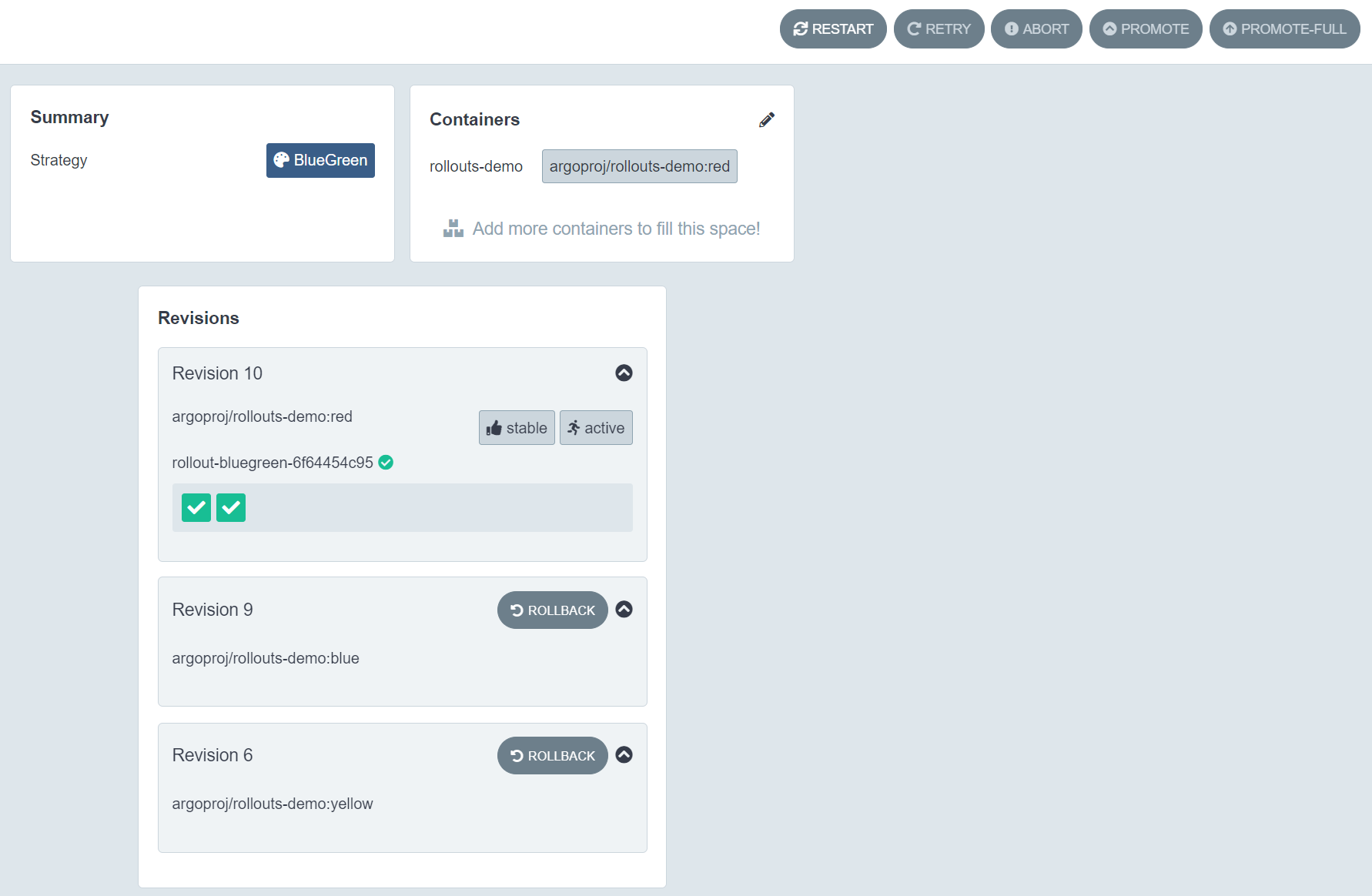
bluegreen
1 | #bluegreen |
Set image:
1 | kubectl argo rollouts set image rollout-bluegreen \ |
Demo
bluegreen
rollout-bluegreen.yaml
1 | # This example demonstrates a Rollout using the blue-green update strategy, which contains a manual |
Canary
ingress.yaml
1 | # apiVersion: networking.k8s.io/v1 |
rollout.yaml
1 | apiVersion: argoproj.io/v1alpha1 |
services.yaml
1 | apiVersion: v1 |
Arago-workflow
1 | #arago-workflow: |
Gitlab-Runner
Docker
1 | #https://docs.gitlab.com/runner/install/docker.html |
Hosted-Machine
Recommend
Notice: Running sudo as gitlab-runner to register
1 | Installing on Linux: |
.gitlab-ci.yml
1 | # default: |
Pipeline UI
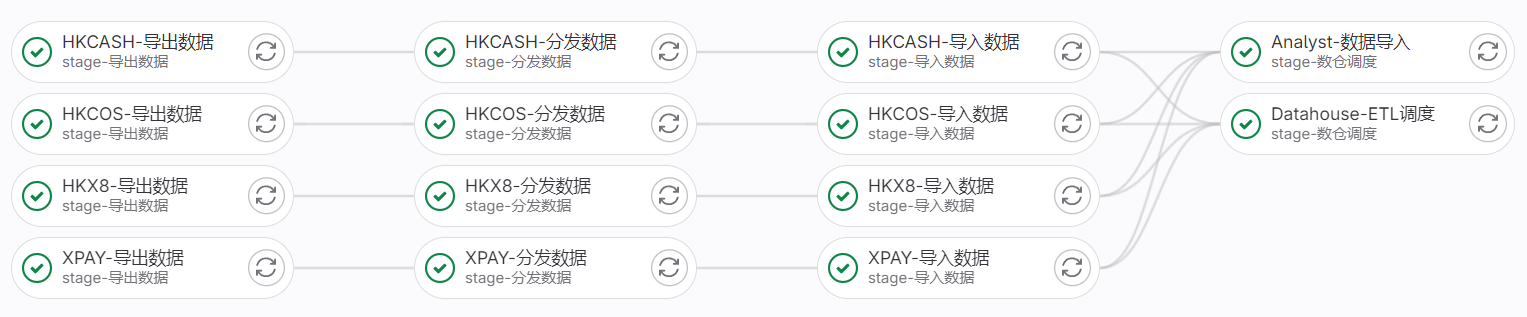
Trigger with remote URL
1 | #https://blog.csdn.net/lenkty/article/details/124668164 |
AutoK3s
Not Recommend, recommend using k3s.
1 | #AutoK3s:(Not Recommend) |